Quick Answer: The dark web hosts 3+ million daily users accessing hidden encrypted networks where 60% of content involves illegal activities—from stolen credentials and malware to explicit content—posing identity theft, cyberbullying, and exposure risks that families can mitigate through parental controls, VPN encryption, and identity monitoring services.
Table of Contents
- Why Dark Web Awareness Matters for Families
- Key Takeaways
- What Is the Dark Web?
- How Does the Dark Web Work?
- Dark Web Content Examples
- Dark Web Risks for Families
- Signs Your Child May Be Accessing the Dark Web
- Family Protection from Dark Web Threats
- Common Dark Web Myths Debunked
- Building Your Family’s Dark Web Defense Strategy
- Frequently Asked Questions
- Sources Used for This Article
Why Dark Web Awareness Matters for Families
The dark web operates as a hidden internet layer requiring specialized tools like Tor to access its encrypted networks. Unlike the surface web Google indexes, this obscure corner harbors both legitimate privacy-focused communications and dangerous illegal marketplaces. Daily users grew from 2 million to over 3 million in March 2025 alone.
Over 24 billion stolen credentials now circulate on dark web markets—up from 20 billion in 2024. Cybercriminals traded $2 billion in Bitcoin transactions through darknet markets in 2024, with fraud shops generating an additional $225 million. With 65% of criminals using dark web data to execute cyber attacks, families face real threats from identity theft to child exploitation.
Key Takeaways
- The dark web comprises encrypted networks accessible only through tools like Tor, hosting 230,000+ active .onion domains with 3+ million daily users as of 2025.
- 60% of dark web marketplaces involve cybercrime activities including stolen data sales, malware distribution, and illegal goods trading totaling $2 billion annually in cryptocurrency.
- Major family risks include exposure to explicit violent content, cyberbullying harassment, identity theft through 24 billion stolen credentials, and malware infections from hacking tools.
- Warning signs children may be accessing the dark web include secretive online behavior, unfamiliar anonymity software like Tor, sudden cryptocurrency interest, and unexplained package deliveries.
- Protect your family with parental control monitoring, VPN encryption for all devices, identity theft protection services, and regular conversations about online safety threats.
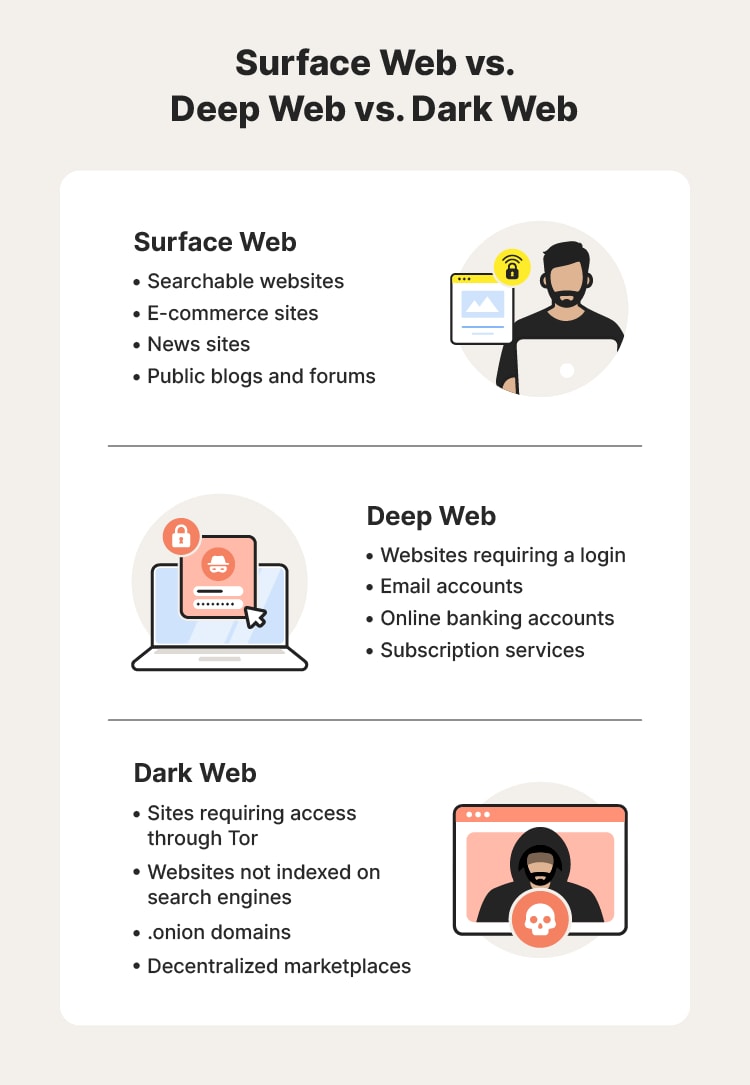
What Is the Dark Web?
The dark web refers to intentionally hidden internet portions requiring specialized tools for access. Unlike the surface web that search engines index, the dark web exists within encrypted networks accessible through software like Tor (The Onion Router) or I2P (Invisible Internet Project).
These tools anonymize user activity by encrypting traffic and routing it through multiple worldwide servers, making tracking nearly impossible. This anonymity explains why the dark web gained its reputation for harboring illicit activities.
Dark Web Scope:
- Size: Estimated at just 0.01% of the total internet
- Daily Users: 3+ million as of March 2025 (up from 2 million at year start)
- Active Domains: 230,000+ .onion sites, though only 4-6% remain consistently accessible
- Geographic Distribution: U.S. leads with 1 million daily Tor users, followed by Germany (600,000) and France (175,000)
The dark web isn’t inherently illegal. It includes forums and platforms serving legitimate purposes—protecting free speech in oppressive regimes or facilitating private communications. However, its anonymity makes it popular with cybercriminals and malicious actors.
How Does the Dark Web Work?
The dark web functions as a hidden internet layer operating outside traditional search engine reach. Accessing it requires specialized tools like Tor that anonymize online activity by encrypting traffic and routing it through multiple servers worldwide. This process conceals identity and location, making movement tracking nearly impossible.
Unlike the surface web, dark web websites use unique “.onion” domain extensions inaccessible without exact URLs. Search engines like Google or Bing don’t index these sites, so accidental encounters don’t occur. This intentional access restriction creates barriers limiting dark web network entry.
How Tor Works:
- Traffic Encryption: Your connection gets encrypted multiple times in layers (hence “onion”)
- Server Routing: Data bounces through random volunteer-run servers (nodes) worldwide
- Exit Point: Final server (exit node) decrypts and sends your request to destination
- Return Path: Response follows same encrypted path back to you
- Identity Protection: Each server only knows previous and next stops—never full route
The dark web’s anonymity attracts diverse users—from journalists and activists seeking safe communication spaces under oppressive regimes to individuals engaged in illegal activities. While visiting the dark web isn’t illegal, many activities within it (illicit marketplaces, data breaches) violate laws.
Dark Web Content Examples
Dark web content varies widely, ranging from legitimate privacy-focused platforms to illegal and highly disturbing materials. Here’s what exists in this hidden internet layer:
Illegal Marketplaces and Criminal Trade
Dark web illegal marketplaces allow anonymous buying and selling of contraband. These underground markets trade in:
Common Illegal Goods:
- Drugs: Recreational substances to prescription medications totaling $470 million in sales
- Weapons: Firearms and illegal weapons (U.S. accounts for 60% of dark web weapon sales)
- Counterfeit Goods: Fake passports, driver’s licenses, and currency
- Stolen Financial Data: Credit card information sells for as low as $25; cards with $5,000 balances cost only $110
- Malware and Hacking Tools: 1,000 premium malware installations available for $5,000
Darknet markets generated over $2 billion in Bitcoin transactions in 2024, with average transaction values climbing 11% to $624. Nearly 37 active marketplaces operated in Q2 2025—a 28% increase from 2024—with the top five platforms handling 72% of all transactions.
Transactions typically use cryptocurrencies like Bitcoin and Monero, adding anonymity layers. New marketplaces emerge every 2-3 weeks despite law enforcement takedowns, which increased 35% in 2024-2025.
Stolen Data and Credential Markets
The dark web serves as a cybercriminal hub for exchanging and selling:
Personal Information Traded:
- Login Credentials: 24 billion unique credentials circulate on dark web markets—up from 20 billion in 2024
- Email and Passwords: 80% of email data has been leaked to the dark web
- Financial Information: Over 1.2 million payment card details were exposed in 2022
- Employee Credentials: Company login data ranks among most-traded items
- Personal Identifiers: Social Security numbers, phone numbers, residential addresses
150,000+ new credentials get indexed daily from stealer logs, breaches, and database dumps. On average, breached data surfaces on the dark web within 7 days of compromise.
Hacking Services Available:
- Ransomware Attacks: Cybercriminals distribute ransomware through dark web channels
- Corporate Espionage: Services for hire targeting business intelligence
- Malware Creation: Tools for creating malware or exploiting software vulnerabilities
- DDoS Attacks: Distributed denial-of-service attack services
This illicit goods and services availability makes the dark web a significant worldwide cybersecurity threat.
Explicit and Violent Content
The dark web hosts disturbing explicit materials that can severely impact psychological health, especially for children who accidentally encounter such content. Graphic imagery, illegal materials, and violent videos exist without the surface web’s regulatory oversight.
Accidental exposure occurs when young internet users stumble upon links shared in forums or chats, potentially leading to anxiety, trauma, or mental health issues requiring professional intervention.
Dark Web Risks for Families
The dark web presents several dangers families should recognize, primarily because its anonymous nature fosters illegal and harmful activities. Children and family members can inadvertently face these risks without proper precautions.
Exposure to Inappropriate and Disturbing Content
Explicit, violent, and disturbing content availability represents one of the dark web’s most significant risks. Unlike the regulated surface web, the dark web contains graphic imagery, illegal materials, and violent videos that can severely affect psychological health—especially in children.
Accidental exposure happens when young internet users encounter links shared in forums or chats. These experiences may trigger anxiety, trauma, or mental health issues requiring professional support.
Protection Strategies:
- Use robust parental control software monitoring online activity
- Educate children about internet safety and potential dangers
- Maintain open communication encouraging kids to report concerning content
- Implement content filtering at router level for household-wide protection
Cyberbullying and Harassment Threats
Dark web anonymity creates environments where cyberbullying and harassment thrive. Individuals hide identities while engaging in targeted attacks—spreading false information, sharing private photos, or sending threatening messages. These attacks profoundly impact emotional wellbeing, leaving victims isolated and vulnerable.
46% of teens experienced cyberbullying in 2024, up from 23.2% in 2021. With over 500,000 online predators active daily, the FBI documented more than 13,000 cases of online financial sextortion targeting minors between October 2021 and March 2023, affecting at least 12,600 victims and linking to at least 20 suicides.
Family Protection Measures:
- Encourage children avoiding personal detail sharing online
- Report suspicious or threatening behavior immediately
- Monitor social media activity and digital communications
- Identify and address potential problems early through involvement
Explore Bark Parental Control App for AI-powered monitoring across 30+ platforms including TikTok, Instagram, and Discord that catch threats traditional filtering misses. For complete device protection, consider the Bark Phone or Bark Watch designed specifically for child safety.
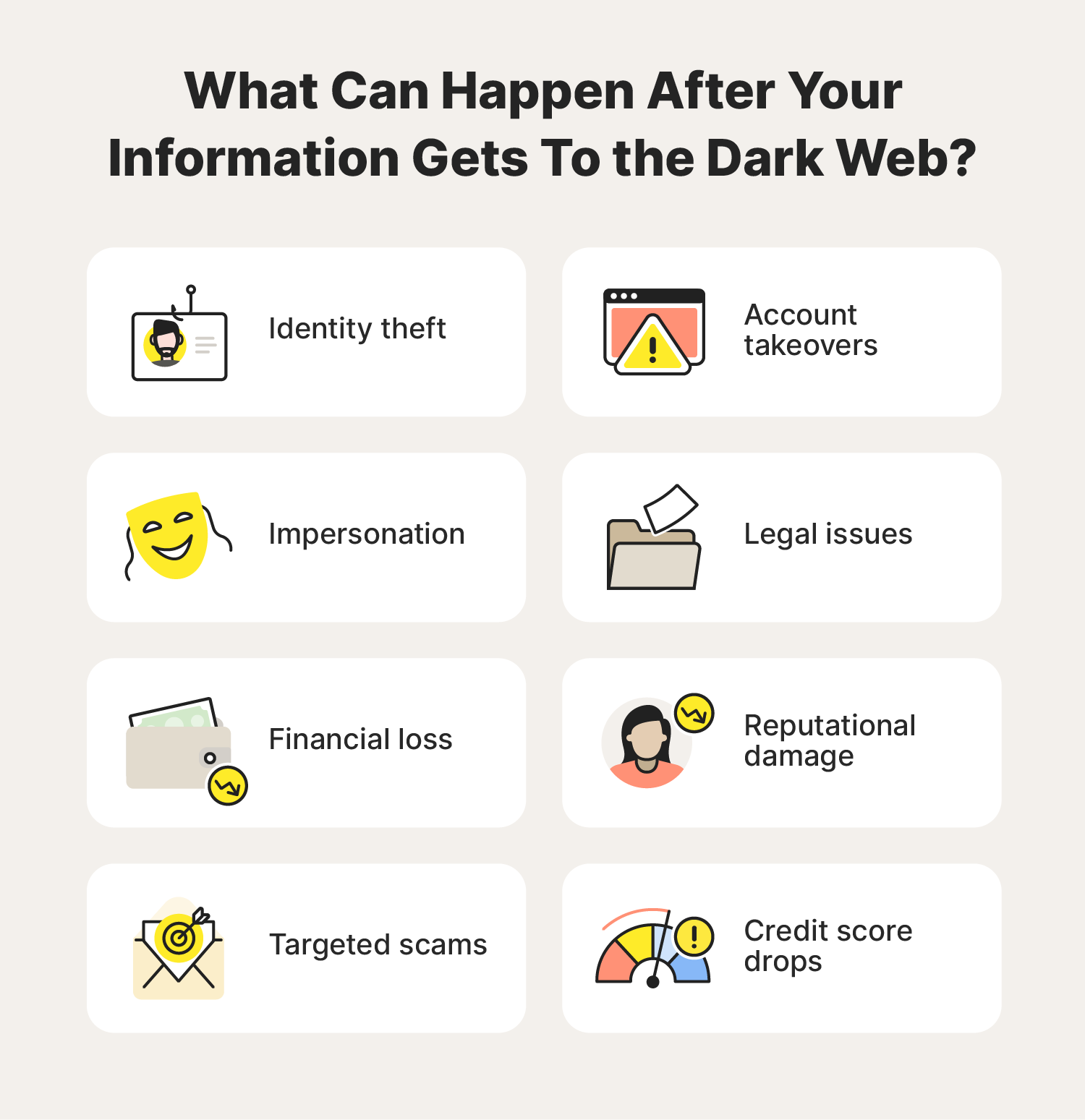
Identity Theft and Financial Fraud
Identity theft represents a prevalent dark web issue where stolen personal data—Social Security numbers, credit card details, login credentials—gets sold in underground marketplaces. Cybercriminals use this information opening fraudulent accounts, making unauthorized transactions, or impersonating individuals online.
Current Identity Theft Landscape:
- Credential Volume: 24 billion unique stolen credentials circulating (2025 data)
- Daily Additions: 150,000+ new credentials indexed daily
- Criminal Usage: 65% of active criminals use dark web data for cyber attacks
- Detection Time: Average 7 days from breach to dark web appearance
- Email Exposure: 80% of email data leaked to dark web
Safeguard Strategies:
- Create strong unique passwords for all accounts
- Enable two-factor authentication everywhere possible
- Monitor financial accounts regularly for suspicious activity
- Subscribe to identity theft monitoring services providing dark web alerts
Services offering identity theft monitoring alert you if sensitive information appears on the dark web, enabling swift action minimizing damage. Check Batten’s identity protection services for comprehensive monitoring solutions.
Malware and Hacking Tool Access
The dark web operates as a marketplace for malicious software, hacking tools, and cybercrime services. Malware purchased on the dark web can infect devices, steal data, or compromise entire systems. Some tools allow hackers remotely accessing and controlling devices without user knowledge.
Available Cyber Weapons:
- Premium Malware: 1,000 high-grade installations for $5,000
- Exploits: Average price $5,345 due to system access impact
- Loaders: Malicious payload delivery tools averaging $3,566
- Ransomware Kits: Ready-to-deploy extortion software
- DDoS Tools: Services overwhelming target networks
Mitigation Practices:
- Keep antivirus software updated with real-time protection
- Avoid suspicious links and untrusted file downloads
- Ensure firewalls protect all household devices
- Teach children about downloading file dangers
- Use VPN encryption preventing network-based attacks
Organizations with compromised credentials on the dark web face 2.56x higher cyber attack risk, while dark web market listings increase incident likelihood by 2.41x.
Signs Your Child May Be Accessing the Dark Web
Parents must recognize potential warning signs indicating children might be venturing into unsafe online territories like the dark web. Below are behaviors and indicators warranting attention, with tips addressing them effectively.
Secretive Online Behavior
The most noticeable red flag is secretive or evasive online behavior. If your child quickly minimizes browser windows, closes tabs, or appears uneasy when you approach while using devices, they may be hiding something.
Reluctance sharing online habits or becoming defensive when asked about internet activity further signals potential dark web usage. Teens naturally seek privacy, but extreme secrecy about digital activities—especially combined with other warning signs—deserves conversation.
What to Watch For:
- Rapidly switching screens when you enter room
- Clearing browser history immediately after use
- Using devices only in private spaces (bedroom, bathroom)
- Refusing to let you see their screen
- Becoming defensive about routine internet questions
Unfamiliar Software and Tools
Specialized software use—such as Tor or anonymity-focused tools—may indicate dark web access attempts. Look for apps or programs you don’t recognize on their devices. These tools typically aren’t required for everyday internet browsing, making their presence possible red flags.
Common Anonymity Tools:
- Tor Browser: Primary dark web access tool with onion logo
- Tails OS: Operating system designed for anonymity
- VPN Services: While legitimate, multiple VPNs suggest hiding activity
- Encrypted Messaging: Apps like Wickr or Session beyond standard messaging
- Virtual Machines: Software creating isolated computing environments
Regularly review apps and software installed on household devices. Have honest conversations if you find programs designed for anonymity, explaining why such tools expose them to unnecessary risks.
Interest in Cryptocurrency
Sudden cryptocurrency curiosity—Bitcoin, Monero, Ethereum—could suggest intent engaging in dark web-associated activities. Due to perceived anonymity, these digital currencies facilitate transactions on dark web marketplaces.
If your child begins acquiring prepaid credit cards or gift cards without explanation, they may attempt purchasing goods or services through untraceable means. The average dark web transaction value reached $624 in 2025, with nearly 20% of vendors using dynamic crypto pricing.
Warning Signs:
- Creating cryptocurrency wallet accounts
- Asking about Bitcoin or crypto purchases
- Researching “anonymous payment methods”
- Receiving cryptocurrency mining software alerts
- Unexplained prepaid card or gift card purchases
Educate your child about cryptocurrency legitimate uses and exploitation for illicit activities. Encourage transparency if they’re using or investing in cryptocurrencies.
Suspicious Packages or Online Interactions
Receiving unexpected or unexplained packages could point to dark web marketplace purchases. Items bought from such platforms often arrive without clear sender information or with generic return addresses.
If your child seems engaging in secretive conversations with strangers online or avoids disclosing interaction nature, investigate further. Dark web criminals often recruit young people through gaming platforms, social media, or forums before moving conversations to encrypted channels.
Red Flags:
- Packages arriving without clear sender information
- Deliveries your child insists on retrieving immediately
- Secretive online conversations they won’t discuss
- New “friends” they’re reluctant to talk about
- Cash transactions or money requests you can’t explain
Look at packages arriving at your home and ask about unusual mail. Monitor your child’s online interactions and encourage them sharing who they communicate with, ensuring safe online behavior engagement.
Family Protection from Dark Web Threats
Staying safe from dark web-associated risks requires proactive measures, informed decision-making, and family education commitment. Below are essential strategies safeguarding your family from dark web threats.
Educate Children About Online Safety
Start with open, age-appropriate conversations about internet dangers and dark web risks. Explain what the dark web is and why it poses dangers, using simple language children understand.
Education Approach:
- Explain dark web basics without creating unnecessary fear
- Teach them avoiding unfamiliar links or unknown source file downloads
- Encourage speaking to you about unusual or disturbing encounters
- Use non-judgmental approach building trust
- Share real-world examples age-appropriately
- Practice “what would you do if…” scenarios
Teach children to critically assess online interactions—a key defense against potential dangers. Educational resources help children grasp broader online risks including scams, phishing attempts, and harmful content.
Review our family cybersecurity plan guide for comprehensive strategies protecting your household’s digital presence.
Monitor Online Activities
Actively monitoring children’s internet use prevents dark web exposure most effectively. Install parental control software blocking harmful website access, tracking browsing activity, and setting online usage time limits.
Monitoring Best Practices:
- Establish clear household internet use rules
- Designate specific online times
- Limit internet access to communal spaces for younger children
- Regularly review browsing histories
- Discuss anything concerning you notice
Top Parental Control Solutions:
| Feature | Bark | Qustodio | iPhone Screen Time |
|---|---|---|---|
| Price | $14/month or $99/year | $55/year (5 devices) | Free (iOS) |
| Platform Monitoring | 30+ apps (TikTok, Instagram, Discord) | 15+ apps with web filtering | Built-in iOS apps only |
| Alert System | Real-time AI alerts for threats | Daily/weekly activity reports | Weekly summaries |
| Content Scanning | AI analyzes messages for 29 risk categories | Keyword filtering | App-level restrictions |
| Screen Time Controls | Basic limits | Comprehensive scheduling | Advanced time limits |
| Best For | Teens on social media (11+) | Younger children (4-12) | Basic iOS device management |
For families with teens active on social media, Bark Parental Control App provides superior protection with AI-powered monitoring catching threats traditional filtering misses. The Bark Phone offers a complete device solution designed for child safety from the ground up. Read our Bark vs Qustodio comparison for detailed analysis.
Secure Your Devices and Data
Keeping household devices secure protects against hacking, malware, and other dark web-related threats. Regularly update operating systems, browsers, and software closing security gaps.
Device Security Checklist:
- Software Updates: Enable automatic updates for OS and all applications
- Strong Passwords: Create unique passwords exceeding 16 characters for each account
- Two-Factor Authentication: Enable 2FA on all critical accounts (email, banking, social media)
- Privacy Settings: Use social media privacy controls limiting public profile access
- Information Sharing: Teach family members safeguarding personal information online
Even seemingly harmless social media posts reveal valuable information to cybercriminals. Limit what you share publicly and teach children the same caution.
Use Identity Theft Protection Services
Consider subscribing to identity theft protection services for added security layers. These services monitor personal information and alert you to suspicious activity—unauthorized data access or appearance on dark web marketplaces.
Protection Service Features:
- Real-Time Monitoring: Tracks your information across dark web marketplaces
- Credit Reporting: Monitors credit file changes and new account openings
- Recovery Assistance: Helps restore identity if compromised
- Dark Web Scanning: Searches for your data in underground forums
- Family Coverage: Protects all household members under single plan
Choose comprehensive plans offering real-time monitoring, credit reporting, and recovery assistance. Some services include tools and educational resources helping families strengthen online safety. Investing in identity theft protection saves time, money, and stress if family data gets compromised.
Explore Batten’s identity protection services for family-focused monitoring solutions.
Encourage Safe Browsing Habits
Teach your family practicing cautious browsing habits. Avoid clicking ads, pop-ups, or suspicious links leading to malware infections or phishing attempts. Stress downloading files only from trusted sources.
VPN Protection Benefits:
Using a VPN (Virtual Private Network) is another essential safety measure. VPNs encrypt internet traffic, preventing hackers from intercepting sensitive data. This proves especially crucial when using public Wi-Fi networks often vulnerable to attacks.
- Military-Grade Encryption: Protects data transmission across all networks
- IP Address Masking: Hides real location preventing tracking
- Public Wi-Fi Security: Secures connections on airport, hotel, café networks
- ISP Privacy: Prevents internet providers monitoring browsing history
- Family Protection: Single subscription covers multiple household devices
NordVPN Complete covers 10 devices for comprehensive family protection, while ExpressVPN offers premium reliability for travelers. Compare NordVPN’s fast private secure option for individual device protection.
Regularly Monitor Financial and Credit Activity
Keep eyes on financial statements and credit reports for unauthorized activity signs. Unexpected charges, new accounts opened in your name, or unexplained credit score changes could indicate identity theft.
Monitoring Schedule:
- Check bank statements weekly for unusual transactions
- Review credit card statements monthly for fraudulent charges
- Pull credit reports quarterly from all three bureaus
- Set up transaction alerts for large purchases or suspicious activity
- Monitor children’s credit if they have SSNs (dark web targets minors)
If you suspect fraudulent activity, act quickly contacting financial institutions and relevant authorities minimizing damage. The faster you respond, the less damage identity thieves can cause.
Common Dark Web Myths Debunked
The dark web often conjures images of hidden lawless networks filled with illegal activities, but not everything fits that stereotype. Many legitimate websites and services exist on the dark web, including secure email providers, whistleblower platforms, and privacy-focused forums protecting user anonymity where privacy is priority.
Access Is Not Illegal, But Activities Can Be
Accessing the dark web through tools like Tor isn’t inherently unlawful. Tor was originally developed for secure communications and remains widely used by journalists, activists, and individuals in oppressive regimes.
However, while visiting the dark web is legal, participating in illegal activities—purchasing stolen data or illicit substances—clearly violates laws. The technology itself is neutral; criminal behavior determines illegality.
Legitimate Dark Web Uses:
- Whistleblower Platforms: SecureDrop enables anonymous source communication
- Encrypted Email: ProtonMail and similar services protect message privacy
- Privacy Forums: Discussions about digital rights and encryption
- Research Access: Academics studying internet freedom and censorship
- Free Speech Protection: Communications in countries restricting internet access
The Dark Web’s True Scale
Contrary to sensational claims, the dark web isn’t as large as often imagined. It comprises just 0.01% of the total internet, vastly overshadowed by the surface web (websites search engines index) and deep web (private databases and intranets).
Size Perspective:
- Surface Web: Indexed by Google, Bing—websites you access daily
- Deep Web: Private databases, email, company intranets—96% of internet
- Dark Web: Encrypted hidden services—0.01% of internet (230,000 active domains)
- Active Sites: Only 4-6% of dark web domains remain consistently accessible
While mysterious, the dark web’s size is limited compared to the vast majority of internet content.
Separating Fact From Fiction
Myths surrounding the dark web lead to misperceptions and unnecessary fear. Distinguishing between legitimate uses and illegal applications proves crucial. Educating yourself and family about what the dark web really is helps you stay informed and better prepared navigating online risks.
Common Misconceptions:
- Myth: “All dark web users are criminals”
Reality: Journalists, activists, and privacy advocates use it legitimately - Myth: “Accessing the dark web puts you on government watch lists”
Reality: Simply using Tor isn’t illegal and doesn’t trigger investigations - Myth: “The dark web is huge and impossible to police”
Reality: It’s 0.01% of internet with regular law enforcement takedowns - Myth: “You’ll accidentally stumble onto the dark web”
Reality: Requires specific software and intentional access—no accidental visits

Building Your Family’s Dark Web Defense Strategy
Staying safe online requires proactive approaches and clear risk awareness. The dark web poses significant dangers—identity theft, harmful content exposure, cyberbullying harassment. However, implementing practical steps like strong security measures, family member education about safe online habits, and internet activity monitoring minimizes these threats.
Your Complete Protection Plan:
- Education First: Open conversations about dark web dangers without creating fear
- Active Monitoring: Parental control software catching threats before they escalate
- Device Security: Updated software, strong passwords, two-factor authentication everywhere
- Identity Protection: Services monitoring for stolen data on dark web marketplaces
- VPN Encryption: Protected internet connections across all household devices
- Financial Vigilance: Regular credit and account monitoring for suspicious activity
Taking advantage of tools like parental controls, VPNs, and identity theft protection provides extra security layers ensuring sensitive information stays private. Open communication within families plays crucial roles preventing unsafe or inappropriate content exposure.
Browse Batten’s cybersecurity marketplace for expert-tested protection tools including Aura All-in-One Digital Security with VPN, identity monitoring, and parental controls in one package, Bitdefender Premium Security with unlimited VPN and full identity protection, or specialized solutions like Cloaked Digital Footprint Eraser for removing personal data from the web. With these steps, you create safer and more secure online experiences for everyone in your household.
Ready to protect your family from dark web threats? Explore Batten’s family safety collection including Aura Parental Controls, Bark monitoring tools, identity theft protection from Identity Guard and IDShield, and VPN encryption with NordVPN Complete—all tested by our cybersecurity experts.
Frequently Asked Questions
Why Is Monitoring Online Activity Important for Family Safety?
Monitoring online activity ensures family members—especially children—aren’t exposed to harmful content or engaging with dangerous platforms like the dark web. Regular oversight allows parents detecting red flags (anonymity-focused tool use) and addressing them early before situations escalate.
How Can a VPN Improve Family Data Security?
VPNs encrypt all internet traffic, ensuring sensitive information (login credentials, personal data) cannot be intercepted by hackers. This proves especially useful protecting devices when using public Wi-Fi networks often vulnerable to man-in-the-middle attacks where criminals steal transmitted data.
What Are Identity Theft Protection Service Benefits?
These services monitor for stolen personal data (credit card information, Social Security numbers) on dark web marketplaces and alert users to suspicious activity. With 24 billion credentials circulating and 150,000 added daily, comprehensive plans include recovery assistance reducing stress and financial loss during breaches.
Are There Legitimate Uses for the Dark Web?
Yes, the dark web hosts platforms protecting user anonymity—whistleblower sites like SecureDrop, secure email providers like ProtonMail, and privacy-focused forums. These tools prove especially valuable in oppressive regimes where free speech is restricted or journalists need protecting sources from government surveillance.
How Can Parental Controls Protect Against Dark Web Risks?
Parental control software blocks harmful website access, restricts unknown source downloads, and monitors children’s browsing activity. These features ensure young internet users remain protected from dark web risks and other online threats by catching concerning behavior before it escalates.
What Should I Do If My Child Shows Interest in Cryptocurrency?
Sudden cryptocurrency interest may indicate attempts engaging in dark web activities where Bitcoin and Monero facilitate anonymous transactions. Educate your child about digital currency legitimate uses while discussing risks associated with using them for anonymous transactions on underground marketplaces.
Sources Used for This Article
- “Dark Web Statistics and Facts (2025),” January 2025, Market.us Scoop, https://scoop.market.us/dark-web-statistics/
- “Dark Web in 2025: Global Usage, Country Curiosity, and Access Trends,” October 2025, PureVPN Research, https://www.purevpn.com/blog/dark-web-statistics/
- “39 Must-Know Dark Web Statistics for 2025,” May 2025, Panda Security, https://www.pandasecurity.com/en/mediacenter/dark-web-statistics/
- “Dark Web Statistics 2025–26: Cybercrime Markets, Breaches & Security Insights,” July 2025, Compare Cheap SSL, https://comparecheapssl.com/dark-web-statistics-cybercrime-trends-market-insights-security-implications/
- “Dark Web Statistics 2025: 2–3M Daily Users, 15B Stolen Credentials,” October 2025, DeepStrike, https://deepstrike.io/blog/dark-web-statistics-2025
- “Dark Web Statistics for 2025: Key Trends and Threats,” September 2025, PrivacySavvy, https://privacysavvy.com/security/safe-browsing/dark-web-statistics/
- “Inside the Dark Web Economy: Key Insights from SOCRadar’s Annual Report 2024,” February 2025, SOCRadar Cyber Intelligence, https://socradar.io/insights-from-socradars-annual-dark-web-report-2024/
- “Cyber Attacks 2024: Data Theft on the Dark Web Increased by 15%,” October 2025, CRIF Cyber Observatory, https://www.crif.com/knowledge-events/press/cyber-attacks-data-dark-web-2024/
- “Tor Metrics: Relay Users by Country,” 2025, The Tor Project, https://metrics.torproject.org/userstats-relay-country.html




