Your password alone isn’t enough to protect you anymore. Cybercriminals know that weak or reused passwords are easy targets, and the numbers back it up.
According to JumpCloud’s 2025 Multi-Factor Authentication (MFA) Statistics & Trends Report, 83% of organizations still rely on password-based logins for at least some resources, while less than 10% of active Google accounts use two-step verification, as reported by Best Reviews. That gap leaves millions of users vulnerable to account takeovers and identity theft, but the fact is that 2FA can stop up to 99.9% of automated attacks – showing just how valuable it is.
So what is 2FA, and why does it matter? Two-factor authentication adds an extra step to the login process by requiring not just something you know (your password) but also something you have (like a phone-generated code) or something you are (like your fingerprint). Think of it as putting both a lock and an alarm system on your digital front door.
This enable 2FA guide will show you how to use two-factor authentication effectively across your most important accounts. With phishing-resistant tools, app-based verification, and biometric options now widely available, setting up 2FA only takes a few minutes – and it could stop hackers cold before they ever get inside your accounts.
Table of Contents
- Key Takeaways
- Understanding Two-Factor Authentication: What Is 2FA?
- Why 2FA Should Be Part of Your Digital Life
- Types of Two-Factor Authentication: Choosing Your Security Method
- Step-by-Step Guide: Enabling 2FA on Your Essential Accounts
- Managing Your 2FA: Backup Codes and Recovery Planning
- Common 2FA Concerns and Solutions
- Advanced 2FA Strategies for Increased Protection
- Taking Action: Your 2FA Implementation Plan
- The Bottom Line on 2FA
- Frequently Asked Questions
Key Takeaways
- Passwords alone leave users exposed, as 83% of organizations still rely on them, and less than 10% of Gmail accounts use two-step verification.
- Two-factor authentication (2FA) works by combining two factors – something you know, have, or are – to block unauthorized access.
- Authenticator apps are considered the gold standard for most users, while hardware keys offer the highest protection for banking and investment accounts.
- SMS codes remain useful when no other option exists, but they carry vulnerabilities such as SIM swap attacks.
- Setting up 2FA should start with email, financial, and social media accounts, then extend to cloud storage and other platforms.
- Backup codes, recovery plans, and routine maintenance are essential to avoid being locked out of accounts.
Understanding Two-Factor Authentication: What Is 2FA?
Two-factor authentication (2FA) requires two different types of verification before granting access to an account. Security experts categorize these factors into three groups: something you know (such as a password), something you have (such as your smartphone), and something you are (such as a fingerprint or facial recognition).
2FA combines at least two of these categories, forcing cybercriminals to bypass multiple barriers instead of just one.
When you log into a 2FA-enabled account, you enter your username and password as usual. The system then requests a second factor, such as a six-digit code from an authenticator app, a push notification, or a biometric scan. Only after completing both steps can you access your account.
This layered approach dramatically reduces risk. Even if attackers obtain your password through a breach, phishing attempt, or password reuse, they cannot log in without the second factor. It functions like a locked door with a guard at the entrance – the key alone is not enough to get through.
The effectiveness of 2FA also lies in its deterrent value. When hackers run automated login attempts and encounter a 2FA prompt, most abandon the effort. Their tools rely on speed and scale, targeting thousands of accounts at once. Introducing friction disrupts these attacks and makes your account a less attractive target.
Why 2FA Should Be Part of Your Digital Life
Recent statistics highlight just how vulnerable personal accounts remain. Statista reported that over 6 billion records were exposed in global data breaches in 2023. Cybercrime losses in 2024 amounted to over $16.6 billion, a whopping 33% increase from 2023.
Consider the domino effect when a primary email account is breached. Attackers can reset passwords for banking, shopping, and social platforms within hours. This access often leads to unauthorized purchases, identity theft, or even fraudulent tax filings. A single weak link becomes the entry point to your entire digital identity.
Families face additional risks. A compromised household account can expose children’s personal details, opening the door to child identity theft. Criminals sometimes exploit minors’ clean credit histories, creating fraudulent accounts that remain hidden until years later.
For remote workers and freelancers, the consequences extend into professional life. Stolen email or cloud storage credentials can put client data at risk, damage business relationships, and create potential liability for mishandling sensitive information.
The financial industry has long embraced 2FA, with most banks requiring it for online transactions. Yet many users overlook enabling 2FA on email and social media, which often provide easier gateways to financial accounts. Securing these high-value entry points is one of the simplest and most effective steps you can take to safeguard your digital life.
Finally, there is a collective benefit. The more individuals adopt 2FA, the harder it becomes for cybercriminals to profit from large-scale attacks. By protecting your own accounts, you also strengthen the broader digital environment, making widespread credential theft less rewarding.
Types of Two-Factor Authentication: Choosing Your Security Method
Understanding the different 2FA methods helps you decide which approach is best for each of your accounts. Each option balances security, convenience, and accessibility differently, and many people use multiple methods depending on the importance of the account being protected.
2FA Methods Comparison Chart
| 2FA Method | Security Level | Convenience | Setup Difficulty | Best For | Main Drawbacks |
| Authenticator Apps | ⭐⭐⭐⭐⭐ | ⭐⭐⭐⭐ | Easy | Most accounts, daily use | Requires smartphone |
| Hardware Security Keys | ⭐⭐⭐⭐⭐ | ⭐⭐⭐ | Medium | Banking, high-value accounts | Cost, limited support |
| SMS Text Codes | ⭐⭐⭐ | ⭐⭐⭐⭐⭐ | Very Easy | Quick setup, older services | SIM swap vulnerability |
| Push Notifications | ⭐⭐⭐⭐ | ⭐⭐⭐⭐⭐ | Easy | Google/Microsoft accounts | Accidental approval risk |
| Email Verification | ⭐⭐ | ⭐⭐⭐ | Very Easy | Backup method only | Email compromise risk |
Authenticator Apps: The Gold Standard
Authenticator apps are the most widely recommended method for everyday 2FA use. They generate time-based, one-time codes that refresh every 30 seconds, creating a moving target for attackers.
Popular apps include Google Authenticator, Microsoft Authenticator, and Authy.
One of the biggest strengths of authenticator apps is that they work offline. Since codes are generated locally on your device, they cannot be intercepted through network attacks or SIM swaps. This makes them far more secure than text message codes.
Backup and recovery are also important considerations. Authy allows multi-device syncing, while Google Authenticator now offers cloud backup on Android. When setting up your app, review backup features and use them to avoid being locked out if you lose your phone.
SMS Text Messages: Better Than Nothing, But Not Ideal
SMS-based 2FA sends codes to your phone via text. While this is a step up from password-only logins, it is vulnerable to SIM swap attacks, where criminals trick carriers into transferring your phone number.
Despite this weakness, SMS 2FA still blocks most mass-attack attempts. The majority of cybercriminals do not carry out targeted SIM swaps, focusing instead on easier wins. If your only option is SMS, it is still worth enabling.
To strengthen SMS 2FA, contact your mobile provider about adding extra verification steps for account changes. Some carriers offer “port protection” or account PINs to block unauthorized transfers. Regularly reviewing your account for suspicious activity also adds another layer of safety.
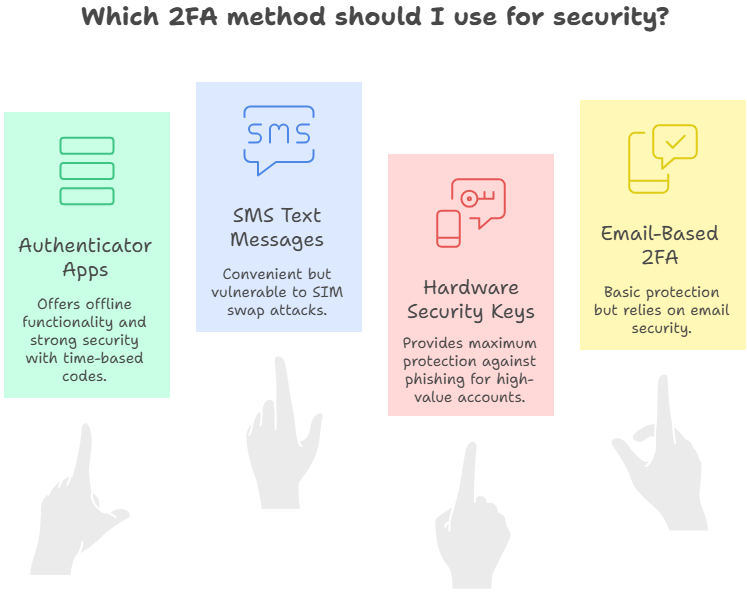
Hardware Security Keys: Maximum Protection for High-Value Accounts
Hardware security keys, such as YubiKey, are physical devices that provide the strongest available form of 2FA. They connect via USB, NFC, or Bluetooth and verify your identity through cryptographic signatures that cannot be intercepted or phished.
Their biggest advantage is protection against phishing. Even if you enter your password on a fake site, the hardware key will refuse to authenticate because it checks the legitimacy of the domain. This makes them ideal for high-value accounts, including online banking, investment platforms, and business-critical systems.
Using hardware keys does require some planning. Purchasing two keys is best practice: one for daily use and another as a backup stored securely. While not every service supports hardware keys, adoption is growing rapidly among banks, tech giants, and enterprise platforms.
Email-Based 2FA: A Stepping Stone Solution
Email-based verification sends a code or link to your registered inbox. While it is an improvement over password-only access, it is generally the weakest form of 2FA because it relies entirely on your email account’s security.
The main issue is circular dependency: if a criminal gains access to your email, they can intercept verification codes for other accounts. Still, for services that do not support stronger options, email-based 2FA offers basic protection against password reuse and mass-automated login attempts.
If you must use email verification, secure your inbox with a strong password and enable a better form of 2FA on your email itself. Treat email-based 2FA as a stopgap, not your primary defense.
| 2FA Method | Security Level | Convenience | Best For | Potential Vulnerabilities |
| Authenticator Apps | High | High | Most users, daily accounts | Device loss (mitigated by backups) |
| Hardware Keys | Highest | Medium | High-value accounts, businesses | Physical loss, limited service support |
| SMS Codes | Medium | High | Basic protection, backup method | SIM swap attacks, network dependency |
| Email Codes | Low-Medium | Medium | Last resort option | Email account compromise |
| Push Notifications | High | Highest | Google/Microsoft accounts | Device compromise, accidental approval |
Step-by-Step Guide: Enabling 2FA on Your Essential Accounts
Setting up two-factor authentication (2FA) follows a similar process across most services, though specific menu names and locations may vary. In general, you will need to access your account’s security settings, locate the 2FA or “login verification” option, choose your preferred method, and complete the setup process.
Getting Started: Your 2FA Setup Checklist
Before you configure individual accounts, prepare the necessary tools and take a systematic approach. Download an authenticator app if you plan to use one.
Google Authenticator and Microsoft Authenticator are both free and available for Android and iOS. Create a secure location for storing backup codes, either within a trusted password manager or written down in a notebook kept in a secure place.
Begin with your most critical accounts first: your primary email, banking and financial accounts, and any platform that stores payment information. These accounts are prime targets for cybercriminals and often serve as gateways to other services through password reset features.
Securing Your Email: The Foundation of Digital Security
Your main email account requires the strongest available 2FA protection because it often functions as the recovery point for your other accounts.
For Gmail users, start by opening your Google Account settings, then select the Security tab and look for 2-Step Verification.
Google provides several 2FA options, including authenticator apps, SMS, voice calls, and hardware keys.
The company also offers “Google prompts,” push notifications sent directly to your registered devices asking you to approve or deny login attempts. These prompts strike a strong balance between security and convenience.
When setting up 2FA on your Google account, you will be asked to provide a backup phone number for account recovery. While useful, this backup number can become a target for attackers. To reduce risk, consider using a secondary phone number or a Google Voice number instead of your main mobile number.
Protecting Your Financial Accounts
Most banks and financial institutions now require 2FA for online services, though the exact implementation varies. Some institutions send SMS codes at every login, while others use risk-based authentication, only requiring 2FA when unusual activity is detected.
Check your bank’s security settings and enable the strongest method available. Many institutions now support authenticator apps or hardware security keys, which offer stronger protection than SMS codes.
If your bank only supports SMS-based 2FA, add extra precautions such as enabling transaction alerts and monitoring your account activity more closely.
Credit card companies and online payment services like PayPal and Venmo typically allow authenticator apps, and many investment platforms support hardware keys.
Because investment accounts often contain significant assets, these should always be protected with the most secure 2FA method available.
Social Media and Personal Accounts
Social media platforms are common targets for cybercriminals since compromised accounts can be exploited for impersonation, scams, and attacks against friends or followers. Facebook, Instagram, LinkedIn, and X (formerly Twitter) all provide 2FA options, usually offering authenticator app support alongside SMS.
When enabling 2FA on social media, review connected apps and services. Many users grant third-party apps access to their accounts, which can sometimes bypass security protections. Regularly review and remove any unnecessary connections to reduce risks.
Cloud Storage and File Sharing Services
Cloud storage accounts often hold sensitive personal data such as family photos, scanned documents, and backups of your devices. Accounts like Google Drive, Dropbox, OneDrive, and iCloud should all be secured with 2FA.
Apple’s iCloud, for example, uses a system that sends verification codes to your trusted Apple devices whenever a new login attempt occurs. This process maintains Apple’s seamless user experience while still offering a strong additional security layer. Dropbox and Google Drive also support authenticator apps and push notifications, which can be configured in just a few steps.
Managing Your 2FA: Backup Codes and Recovery Planning

Enabling two-factor authentication (2FA) is only the first step. To make it reliable, you also need a plan for account recovery. Every major service that supports 2FA provides backup codes, and these codes are your lifeline if your main authentication method becomes unavailable.
When you activate 2FA, download the backup codes immediately and store them securely. Providers typically generate a set of 8-10 single-use codes that work exactly like your usual 2FA method. Treat them with the same care as your passwords – never leave them unprotected or in easily accessible places.
Password managers are a smart option for storage. Most modern managers include encrypted “secure notes” where you can safely keep backup codes, recovery keys, and other sensitive information. This keeps everything in one protected place while remaining easy to access when needed.
For your most important accounts, such as email and banking, create a physical backup as well. Writing codes down and keeping them in a fireproof safe or with other essential documents ensures access even if you lose all digital devices at once.
Common 2FA Concerns and Solutions
Although 2FA is highly effective, many users hesitate to enable it due to concerns about convenience or lockouts. Understanding common issues – and how to solve them – helps you use 2FA without frustration.
What If I Lose My Phone?
Losing your phone doesn’t mean losing your accounts. Most authenticator apps now offer cloud sync or account recovery features, so codes can be restored on a new device.
Backup codes fill the gap immediately, giving you time to reconfigure your new phone.
Some services also allow multiple 2FA methods, such as both an authenticator app and SMS, giving you another layer of redundancy.
Is This Too Inconvenient for Daily Use?
Modern systems have made 2FA far less intrusive. Trusted device settings and risk-based authentication mean you typically only need to verify when signing in from a new device or unusual location.
On your regular phone or computer, you may rarely be asked for a code. Once the setup becomes routine, most users find the added seconds at login are well worth the protection from account takeovers.
What About Family Sharing and Multiple Users?
Shared accounts or family devices require a slightly different approach. Instead of sharing personal credentials, use built-in family management systems like Google Family Link, Apple Family Sharing, or Microsoft Family. These allow shared access without compromising individual account security.
If an account must be shared directly, keep backup codes and 2FA details stored securely in a place accessible to all authorized users. Update this information whenever 2FA methods change to avoid being locked out unexpectedly.
Advanced 2FA Strategies for Increased Protection
After setting up basic two-factor authentication (2FA), you can strengthen your security further with more advanced strategies. These methods help ensure that your most sensitive accounts receive the highest level of protection while keeping daily use practical.
Risk-Based Account Prioritization
Not every account carries the same level of risk. Focus your strongest 2FA methods on the accounts that would cause the greatest damage if compromised. For example, use hardware security keys for banking, investment, and retirement accounts.
Rely on authenticator apps for email and social media, where compromise can lead to account takeovers or phishing attempts. For less critical accounts, such as subscriptions or forums, SMS-based 2FA can serve as a last-resort option when other methods are unavailable.
This tiered approach helps you allocate your security resources wisely. By assessing which accounts store financial information, personal data, or business access, you can protect what matters most without adding unnecessary friction to your daily logins.
Integration with Password Management
Password managers are increasingly integrating 2FA functionality, allowing you to store both login credentials and one-time codes in a single encrypted application. While some security experts prefer separating passwords and 2FA codes, many users benefit from the balance of security and convenience this approach offers.
When evaluating password managers, look for solutions that support local authenticator features, secure backup of 2FA seeds, and strong encryption standards. Integrated systems can simplify login processes across multiple devices while reducing the risk of losing access if your phone or authenticator app fails.
Monitoring and Maintenance
Strong 2FA protection requires ongoing attention. Many users set up 2FA once and never revisit it, which can leave them vulnerable to expired backup codes, outdated recovery options, or forgotten app authorizations.
Make 2FA reviews part of your regular cybersecurity routine. Check quarterly to ensure backup codes are current, recovery emails and phone numbers are up to date, and unauthorized apps or devices are removed.
This routine maintenance ensures your protections stay aligned with updates from service providers and changes in your own devices.
Taking Action: Your 2FA Implementation Plan
Two-factor authentication remains one of the most effective ways to prevent account compromise. It adds an additional layer of defense that blocks many common attack methods, even when passwords are exposed.
Begin by securing your three most critical accounts: your main email, your primary financial account, and your most-used social media profile. These accounts typically serve as gateways to other services and are the most attractive targets for criminals.
Once you are comfortable using 2FA daily, extend it to other accounts in order of importance, such as online shopping, work tools, or cloud storage.
Each new account you protect reduces the chance that attackers can pivot from one service to another. In doing so, you not only protect your own information but also shield your contacts, clients, or family members from potential attacks launched through compromised accounts.
The Bottom Line on 2FA
Two-factor authentication is a necessity for protecting your digital accounts. With billions of records exposed in breaches and cybercrime losses climbing past $16 billion in 2024, the risks of relying on passwords alone are too high.
2FA adds a critical extra barrier, blocking up to 99.9% of automated attacks and deterring criminals from targeting your accounts.
By using the right mix of methods – authenticator apps, hardware keys, or SMS – you can tailor security to fit your needs.
Regularly updating backup codes, reviewing connected apps, and prioritizing high-value accounts ensures long-term protection. Start with your email, banking, and social media, then expand coverage gradually. With thoughtful planning, 2FA becomes a simple but powerful tool for securing your digital life.
Ready to protect your digital life comprehensively? Explore our expertly vetted cybersecurity tools and comprehensive protection solutions at Batten Cyber’s trusted marketplace. From password managers with integrated 2FA to complete identity protection services, we’ve researched and recommended the tools that make digital security simple and effective for families and individuals.
Frequently Asked Questions
What Is the Difference Between 2FA and MFA?
Two-factor authentication (2FA) requires exactly two verification factors, while multi-factor authentication (MFA) can involve two or more. MFA may include additional checks like security questions, geolocation analysis, or adaptive authentication that responds to login behavior. While 2FA is sufficient for most personal accounts, MFA is often recommended for enterprise environments where multiple layers of verification better protect sensitive systems.
Can Biometric Authentication Replace Other 2FA Methods?
Biometrics like fingerprints or facial recognition are strong security factors, but they should not stand alone. Unlike a password, biometric data cannot be changed if compromised. Experts recommend combining biometrics with another factor, such as a hardware key or authenticator app. This layered approach ensures that if biometric data is stolen or spoofed, attackers cannot gain full access to your accounts.
How Does 2FA Protect Against Phishing?
2FA blocks most phishing attempts by requiring a second factor the attacker does not have. For example, if you mistakenly enter your password on a fake login page, the criminal still cannot log in without your authenticator code or hardware key. Phishing-resistant methods like FIDO2 hardware keys add even stronger protection by verifying the legitimacy of the website before completing authentication.
Is It Safe to Use 2FA on Public Wi-Fi?
Yes, 2FA is safe to use on public Wi-Fi and actually provides extra protection in these higher-risk environments. Even if someone intercepts your network traffic, authenticator codes generated on your device cannot be reused. Hardware keys and push notifications are also safe on public networks because they rely on cryptographic checks or direct device approval rather than data transmitted in plain text.
What Happens If a Service I Use Does Not Support 2FA?
If a platform does not offer 2FA, strengthen your protection with unique, complex passwords stored in a password manager. Turn on account monitoring services or enable login notifications if available. Regularly check for updates, since many companies eventually add 2FA options. If the service stores highly sensitive data and still lacks 2FA, consider switching to a more secure provider.
How Do Businesses Benefit from Enforcing 2FA for Employees?
For businesses, 2FA reduces the risk of account takeovers that can lead to data breaches, financial fraud, and compliance violations. Employees often reuse passwords across platforms, making them easy targets for attackers. By enforcing 2FA, companies block most credential-stuffing and phishing attempts, strengthen regulatory compliance, and build trust with clients. Many organizations adopt hardware keys or enterprise-level authenticator solutions to secure employee accounts.
Sources
- 2025 Multi-Factor Authentication (MFA) Statistics & Trends to Know
- The Majority of Gmail Users Still Don’t Use 2FA – Best Reviews
- https://secureframe.com/blog/fbi-internet-crime-report-2024#:~:text=In%202024%2C%20the%20IC3%20received,%2412.5%20billion%20reported%20in%202023.
- Use Two-Factor Authentication To Protect Your Accounts | Consumer Advice




